|
Home
Summary
Introduction
DeSIRE
& DeFINE
DeSIRE
DeFINE
Initial
Steps
Events
Related
Projects
Links
Literature
|
DeSIRE
(DEpendable
Systems and Information infrastructures
- Research and Exploitation)
17 November 2002
Here we
provide a first expansion of what was said about the
proposed DeSIRE IP in the document “Dependability in
Framework Programme 6”, of 4 November 2002. As that
document explained, one possibility is to structure the
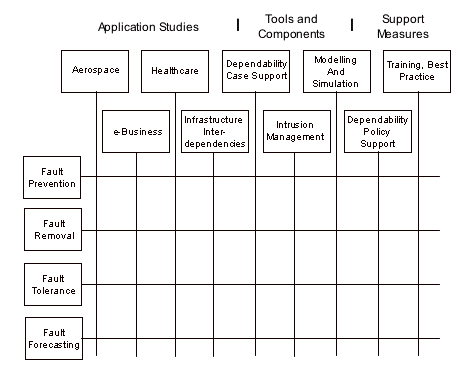
DeSIRE IP using a matrix organization, as used by various
companies that undertake multiple large system
implementation projects. Such projects typically make use of
(and challenge the limits of) a number of software and
perhaps also hardware technologies. A matrix organization
facilitates both co-ordination across projects, and
technology development. In DeSIRE’s case the matrix
columns will correspond to major sub-projects, the rows to
particular dependability-related technologies - see
illustrative diagram below.
At this
stage we simply identify four technology rows in the matrix:
rigorous design, at both the architectural and at various
design levels (i.e. fault prevention); verification and
validation (i.e. fault removal); fault tolerance (of both
accidental and malicious faults); system evaluation (i.e.
fault forecasting). Each given row represents activities
aimed at (i) the deployment and refinement of any relevant
tools and components, (ii) the provision of advice on their
use, and (iii) the assessment of how effectively they are
used in each relevant sub-project, and hence of their
strengths and shortcomings.
Such a
matrix would develop as the IP progresses and takes on
additional sub-projects and starts considering additional
dependability issues. At least three types of sub-project
can be envisaged: application case studies, generic tool and
component developments, and support measures. However, from
the Expressions of Interest so far received, one can already
envisage DeSIRE undertaking an initial set of major
sub-projects such as is described below.
Application
Case Studies
One planned
category of major sub-projects is that of application case
studies, ideally resulting in realistic demonstrator
systems, designed to address new challenges and complement
various aspects of current dependability practice. The aim
in each case would be to find how best to make effective use
of the most suitable current dependability technologies, so
as to achieve the particular dependability attributes
required.
Our aim is
to have a small number of such case studies, each from a
different application domain, which together provide a
representative set of challenges and opportunities, and an
effective means of furthering the cause of dependability in
e-Europe, so-to-speak. Ideally, these case studies will be
undertaken mainly by DeSIRE partners who have
directly-related plans for full-scale development efforts.
Such partners can thus ensure that case study specifications
are adequately realistic, and that there is a reasonably
direct exploitation channel for any results obtained and
lessons learned.
The set of
possible application studies – most of which are
likely to concern the problems of computer-based systems
(i.e. systems involving humans as well as computers) rather
than just the technical problems associated with computer
and communications hardware/software – could for
example include ones in:
Aerospace: Most companies
working in this domain are well experienced in the use of
current fault management techniques and tools, though
these are being challenged by the growth of system
functionality and complexity, so the need for further
dependability, and in particular safety, R&D is
well-accepted. This need is particularly pressing given
likely huge future systems involving worldwide networking
and inter-working.
e-Business:
for example the domain of large scale networked systems
for business process integration, accounting, enterprise
planning, etc. This is a very important application area,
in which issues of dependability, and in particular of
security of critical assets and business process
availability in the face of intrusions from elsewhere in
the worldwide network, and of actions by corrupt
insiders, are becoming an ever-greater challenge.
Healthcare:
for example related to information systems covering
hospitals, drug supply and public health provision. With
such systems, issues of the overall acceptability and
effectiveness of the functionality provided, and in
particular of the system’s mechanisms for achieving
reliability and ensuring confidentiality, can pose very
difficult socio-technical as well as technical
challenges. (Additional major problems arise from the
huge extent and the semi-structured nature of the
information that has to be dealt with, and the need to be
able to cope with all sorts of emergency situations.)
Interdependent
Infrastructures: Europe’s power and water
utilities, say, and its information infrastructure, have
many interdependencies, of various types. These
interdependencies form the potential sources for faults,
and thus may need to be removed if at all possible unless
means can be found for tolerating their effects. A set of
interconnected infrastructures is itself a system, and in
principle existing means of computer system modelling and
analysis should be of direct applicability for assessing
system-of-system dependability, at least as far as
discrete behaviour of the information and other
infrastructures is concerned. In practice issues of size
and complexity may require new methods and tools.
Co-operation between researchers in computer system
dependability assessment, and those in infrastructure
interdependency analysis, could thus be mutually
beneficial. However, undertaking a full analysis of
Europe’s critical infrastructures would be
inappropriate for an IST R&D project, given the
nature – as well as the scale – of the work
that this would involve.
Needless to
say, the above choice of examples is at this stage really
just meant to be illustrative, since further consideration,
and negotiations with prospective partners, could well
result in significant changes to the above list.
Tools
and Components
Another
category of sub-project that we can envisage will be
concerned with the development of new or improved
dependability-related tools and components. The possible
range of such tools and components is very large. Here we
mention just three:
Dependability Case Support: The concept of a
safety case readily generalizes to that of a
dependability case, i.e. the set of arguments and
evidence justifying any claims that are made about a
given system’s future dependability. Tool support
is needed for the creation, maintenance and analysis of
such dependability cases, and in particular for assessing
trade-offs between the various dependability attributes
(e.g. availability and confidentiality), and for ensuring
design traceability between dependability cases and
system design decisions.
Intrusion
Management: There is a need for generic system components
that complement and enhance conventional intrusion
detection techniques, through helping to minimize the
harm and disruption caused by intrusions, and ideally
even to mask their effects entirely, so that normal
service can be continued while any damage is repaired and
the sources of the intrusions are identified and dealt
with.
Modelling
and Simulation: There is a need for generic modeling
tools capable to being used to simulate the dependencies
between infrastructures, so as to assess fault
propagation and their consequences on system
failures.
Support
Measures
Two likely
sub-projects in this category concern (i) dependability
policy support, and (ii) training, technology assessment,
and encouragement of best practice. Dependability RTD in FP6
needs to relate not just to commercial and societal needs
and to technology developments, but also to the world of
government and multi-national industry policy-making. DeSIRE
therefore also should provide support for effective
dialogues between relevant policy makers and the
dependability research communities - ideally so that each
can learn from and influence the other. Similarly, DeSIRE
must try to promulgate current best practice far beyond its
own set of partners, in particular to many other industrial
and government organisations working on turning the e-Europe
plans into reality, based on assessment of the developed
technologies with regard to project objectives and to
interoperability, and where relevant involving the promotion
of open source.
Concluding
Remarks
Repeating a
statement made in our document of 4 November, the initial
partial formulation we have for DeSIRE’s “vision”
is that over the next five-ten years:
(i) European industry should become capable of
creating large scale ICT applications and services that
demonstrably provide guaranteed and appropriately
balanced levels of security, safety, availability,
survivability, etc. based where appropriate on a
warranted non-proprietary (open source) general purpose
information infrastructure,
(ii)
means will have been found for providing controlled and
trustworthy evolution of the European information
infrastructure, as networking becomes ever more
pervasive, and new services are being used by very large
numbers of often mobile and/or untrained users, and
(iii) an
understanding will have been gained of the dependence of
Europe’s various other critical infrastructures on
the global information infrastructure, and appropriate
measures taken to remove, or to tolerate the consequences
of, undesirable interdependencies.
This
present document has been prepared as an additional input to
the discussions to be held at the upcoming DeSIRE/DeFINE
Workshop (Pisa, 25-27 November). We must re-iterate that the
discussion it provides is aimed merely at conveying in
somewhat more detail than hitherto the general aims and
intended style of the proposed DeSIRE IP, not at pre-empting
decisions regarding its work plan, detailed preparation of
which will start after the Workshop.
Tom
Anderson
Brian Randel
 l l
|